ENCRYPTION_KEY, AUTH_SECRET, DB_CONNECTION_URI and REDIS_URL must be defined.
However, you can configure additional settings to activate more features as needed.
General platform
Used to configure platform-specific security and operational settingsMust be a random 16 byte hex string. Can be generated with
openssl rand -hex 16Must be a random 32 byte base64 string. Can be generated with
openssl rand -base64 32Must be an absolute URL including the protocol (e.g. https://app.infisical.com).
Data Layer
The platform utilizes Postgres to persist all of its data and Redis for caching and backgroud tasksPostgres database connection string.
Configure the SSL certificate for securing a Postgres connection by first encoding it in base64.
Use the command below to encode your certificate:
echo "<certificate>" | base64Redis connection string.
Email service
Without email configuration, Infisical’s core functions like sign-up/login and secret operations work, but this disables multi-factor authentication, email invites for projects, alerts for suspicious logins, and all other email-dependent features.Generic Configuration
Generic Configuration
Hostname to connect to for establishing SMTP connections
Credential to connect to host (e.g. team@infisical.com)
Credential to connect to host
Port to connect to for establishing SMTP connections
If true, use TLS when connecting to host. If false, TLS will be used if STARTTLS is supported
Email address to be used for sending emails
Name label to be used in From field (e.g. Team)
Twilio SendGrid
Twilio SendGrid
- Create an account and configure SendGrid to send emails.
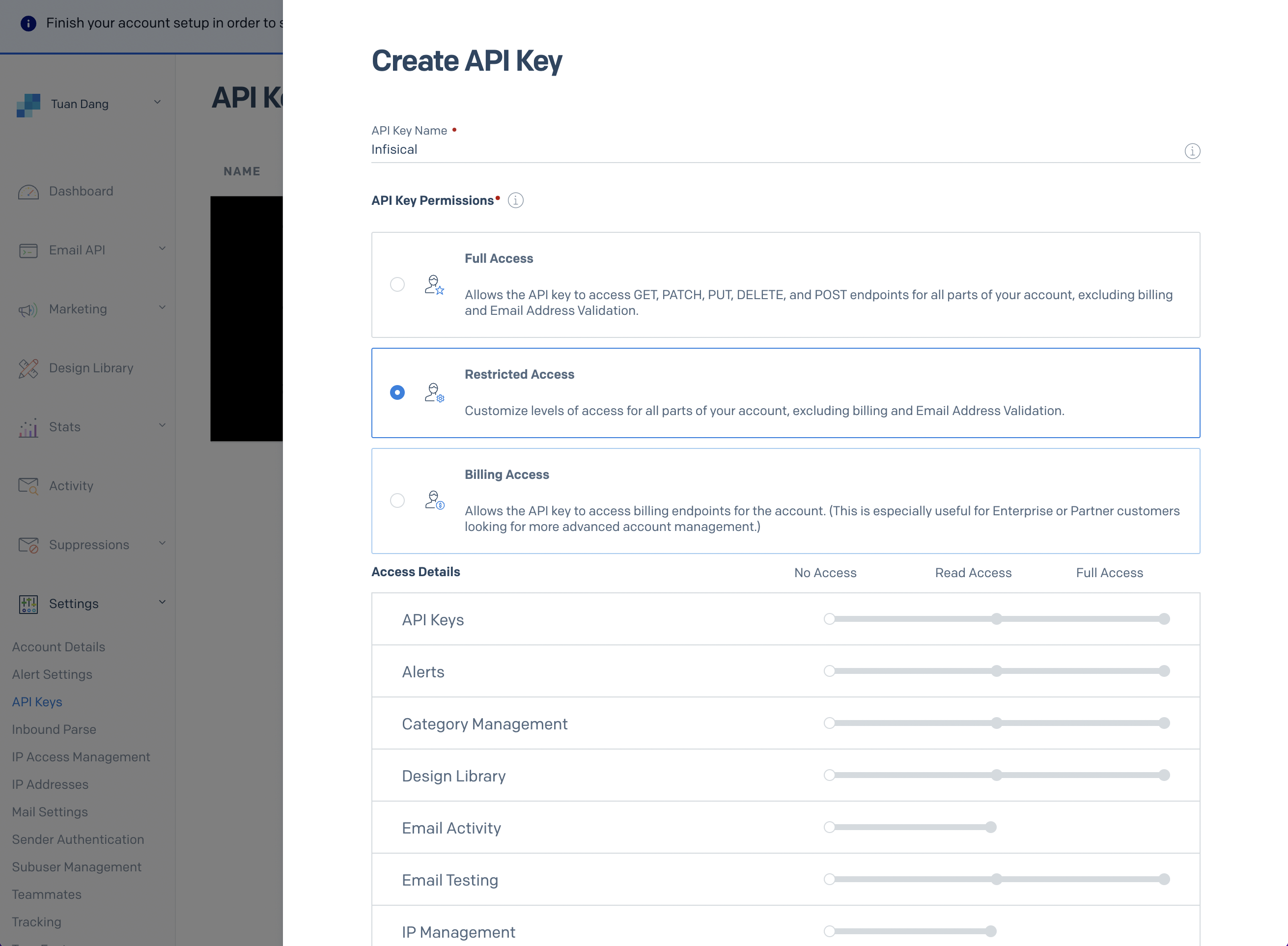
- Create a SendGrid API Key under Settings > API Keys
- Set a name for your API Key, we recommend using “Infisical,” and select the “Restricted Key” option. You will need to enable the “Mail Send” permission as shown below:
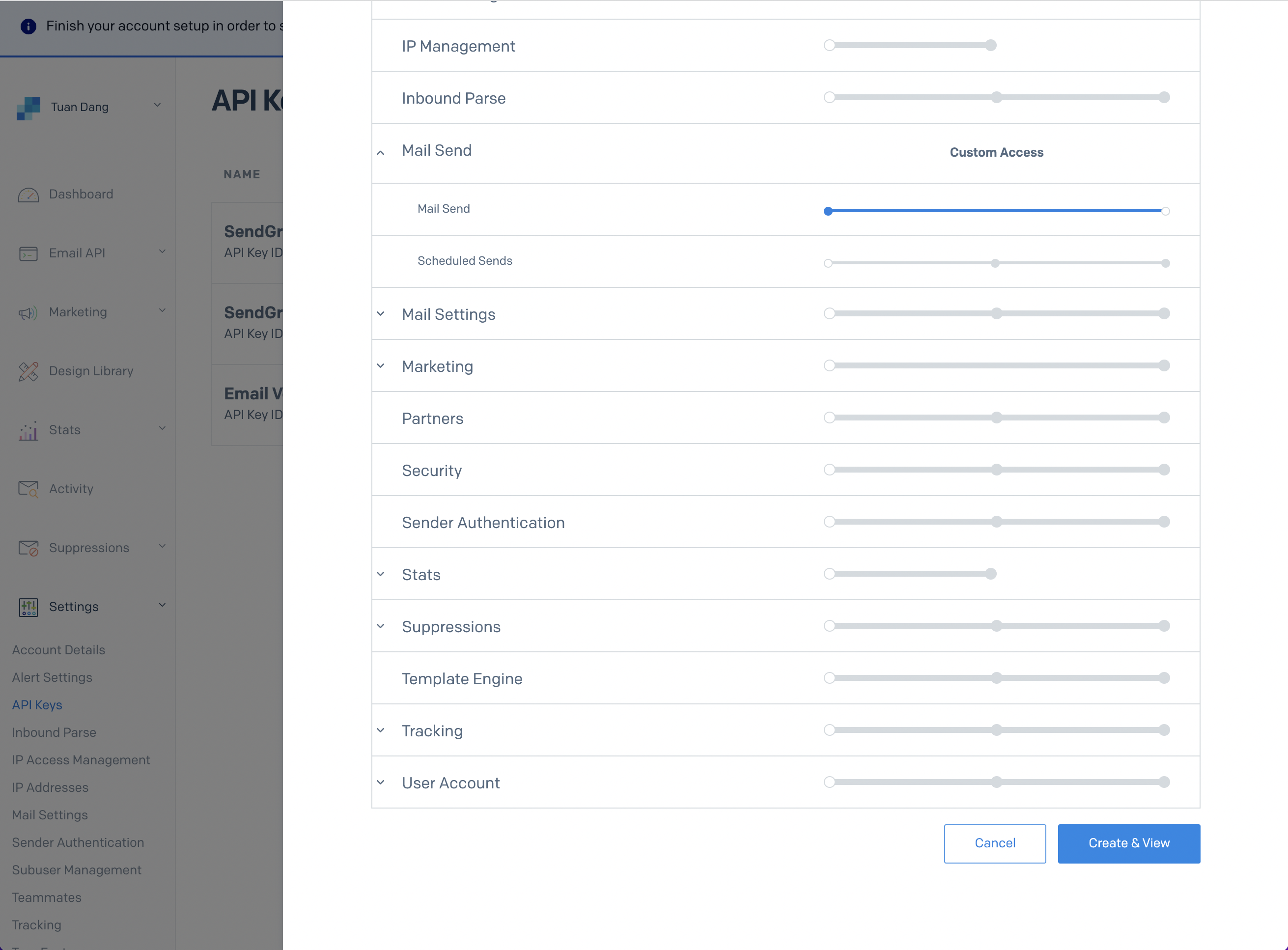
- With the API Key, you can now set your SMTP environment variables:
Remember that you will need to restart Infisical for this to work properly.
Mailgun
Mailgun
- Create an account and configure Mailgun to send emails.
- Obtain your Mailgun credentials in Sending > Overview > SMTP
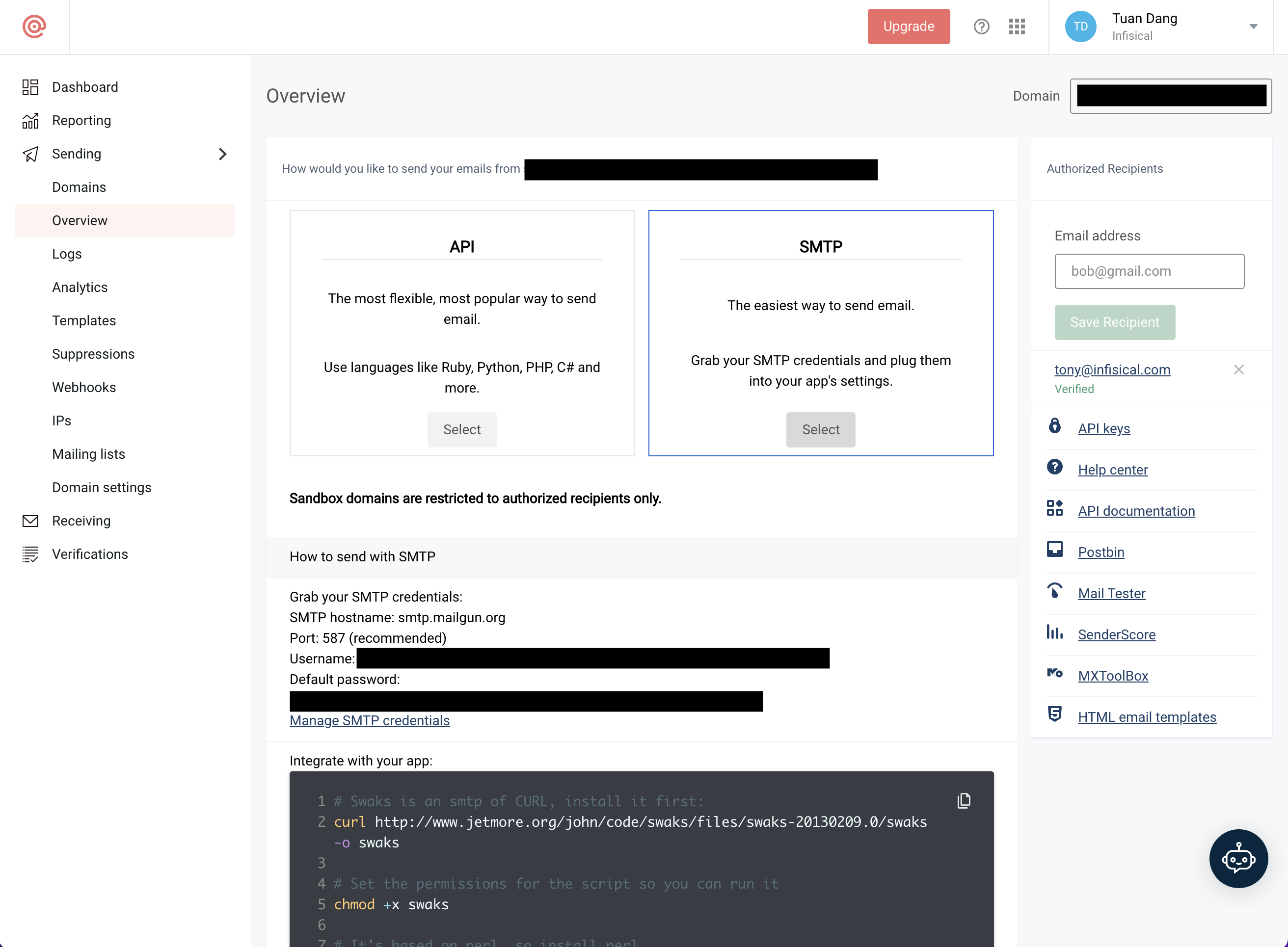
- With your Mailgun credentials, you can now set up your SMTP environment variables:
AWS SES
AWS SES
Create a verifed identity
This will be used to verify the email you are sending from.
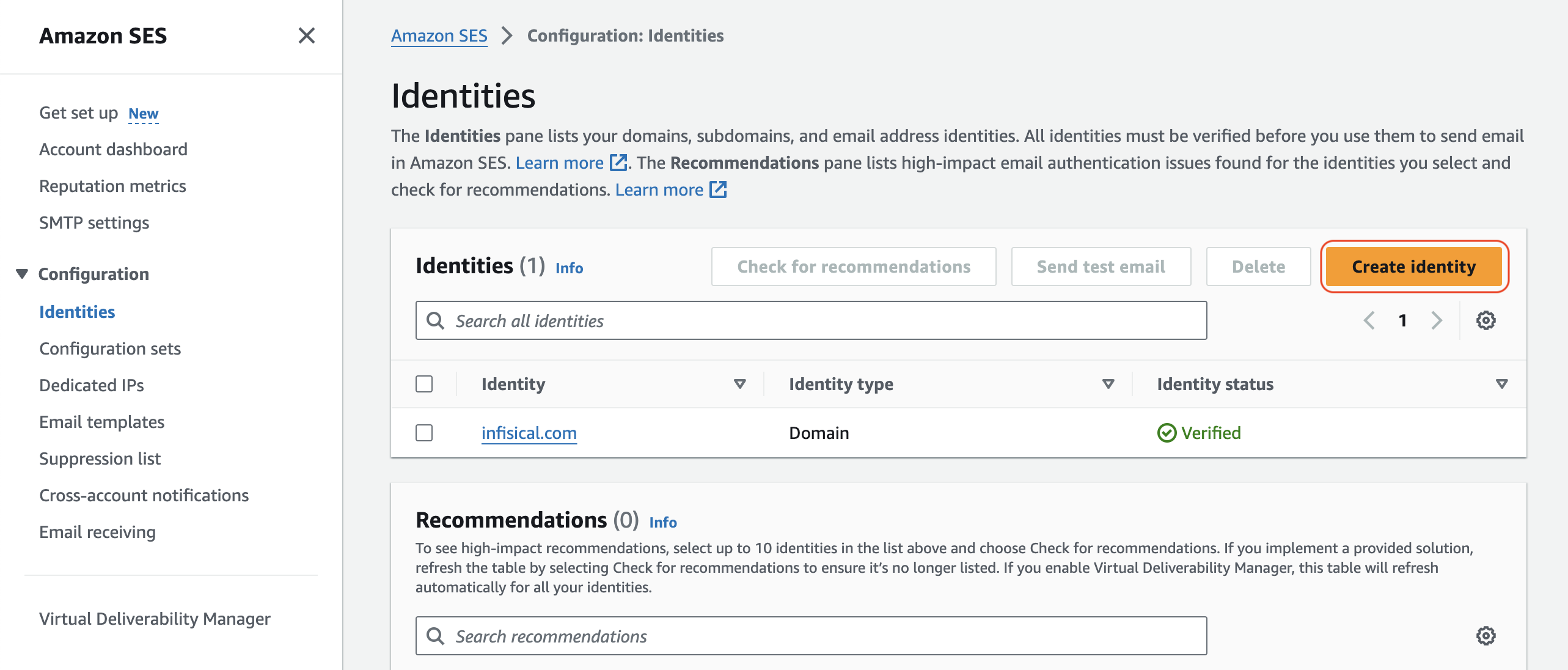

If you AWS SES is under sandbox mode, you will only be able to send emails to verified identies.
Create an account and configure AWS SES
Create an IAM user for SMTP authentication and obtain SMTP credentials in SMTP settings > Create SMTP credentials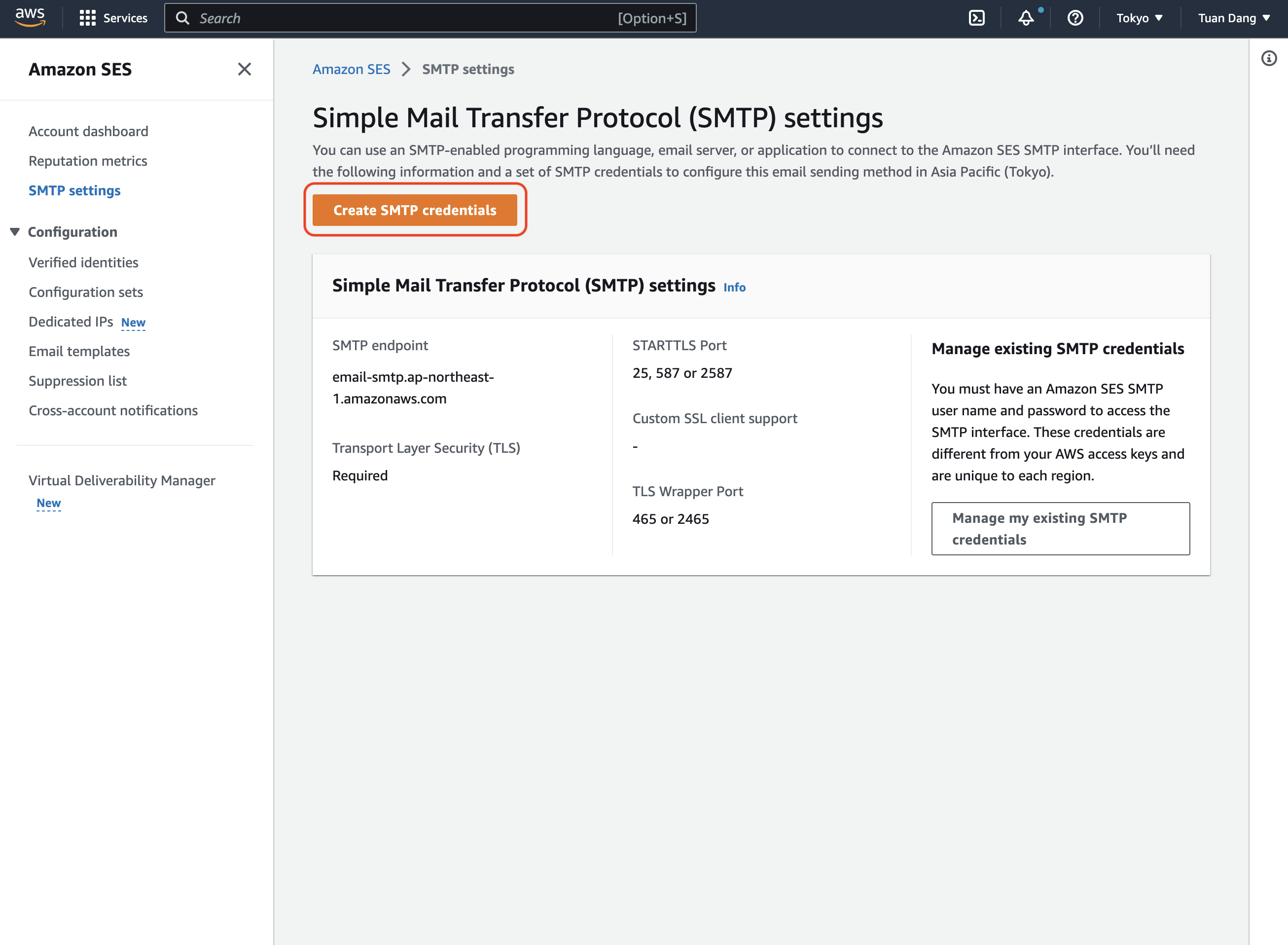
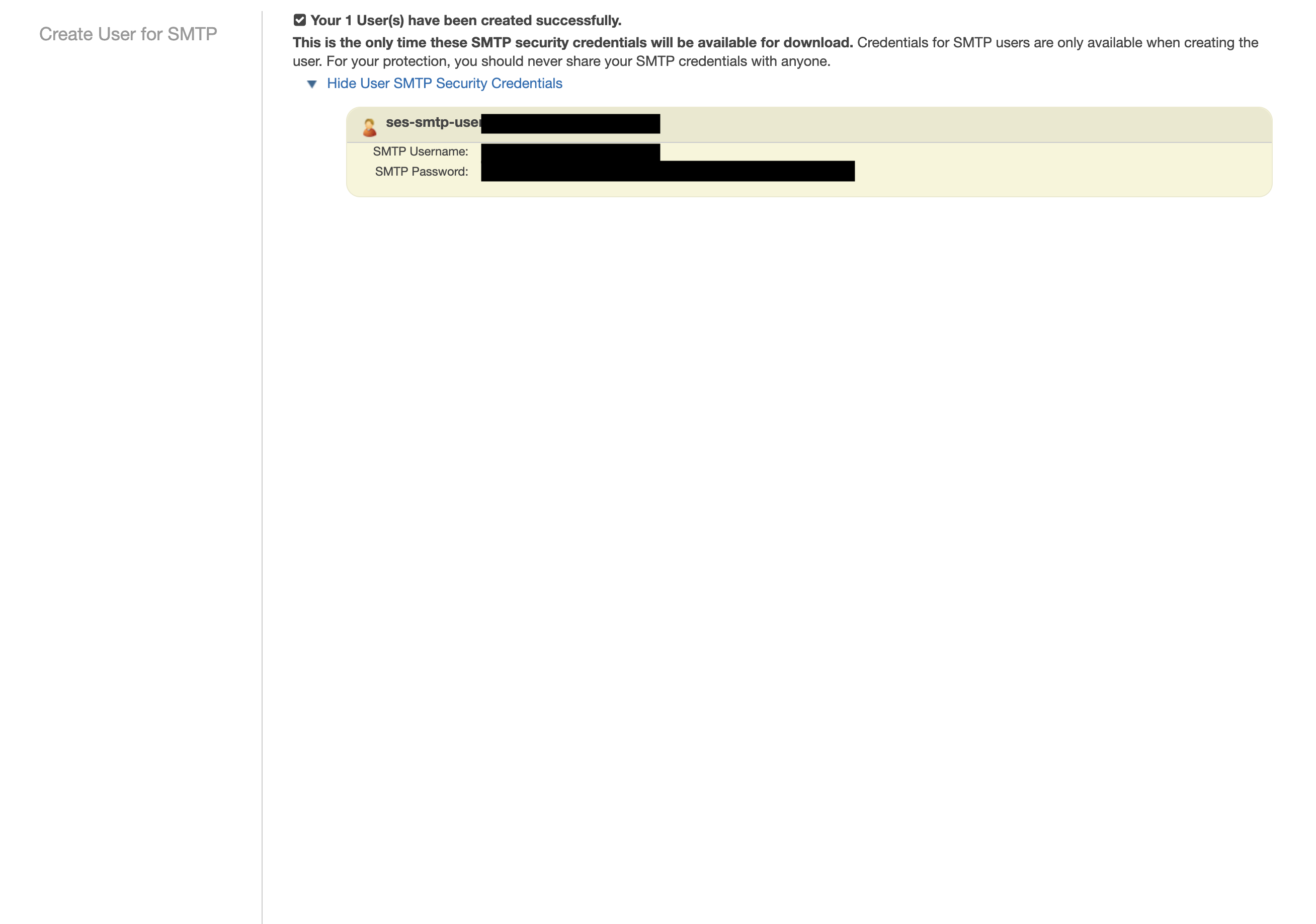


Remember that you will need to restart Infisical for this to work properly.
SocketLabs
SocketLabs
- Create an account and configure SocketLabs to send emails.
- From the dashboard, navigate to SMTP Credentials > SMTP & APIs > SMTP Credentials to obtain your SocketLabs SMTP credentials.
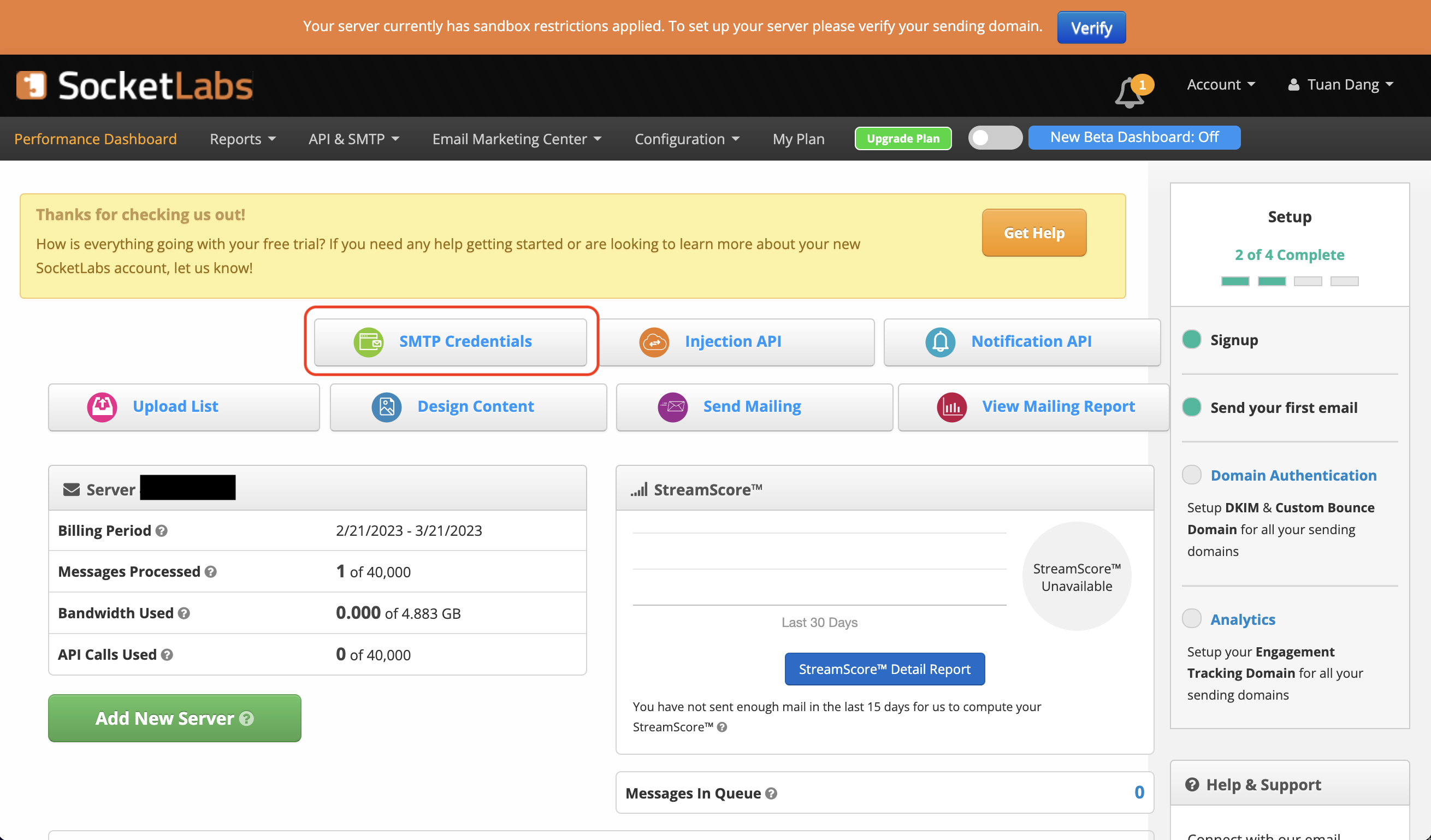
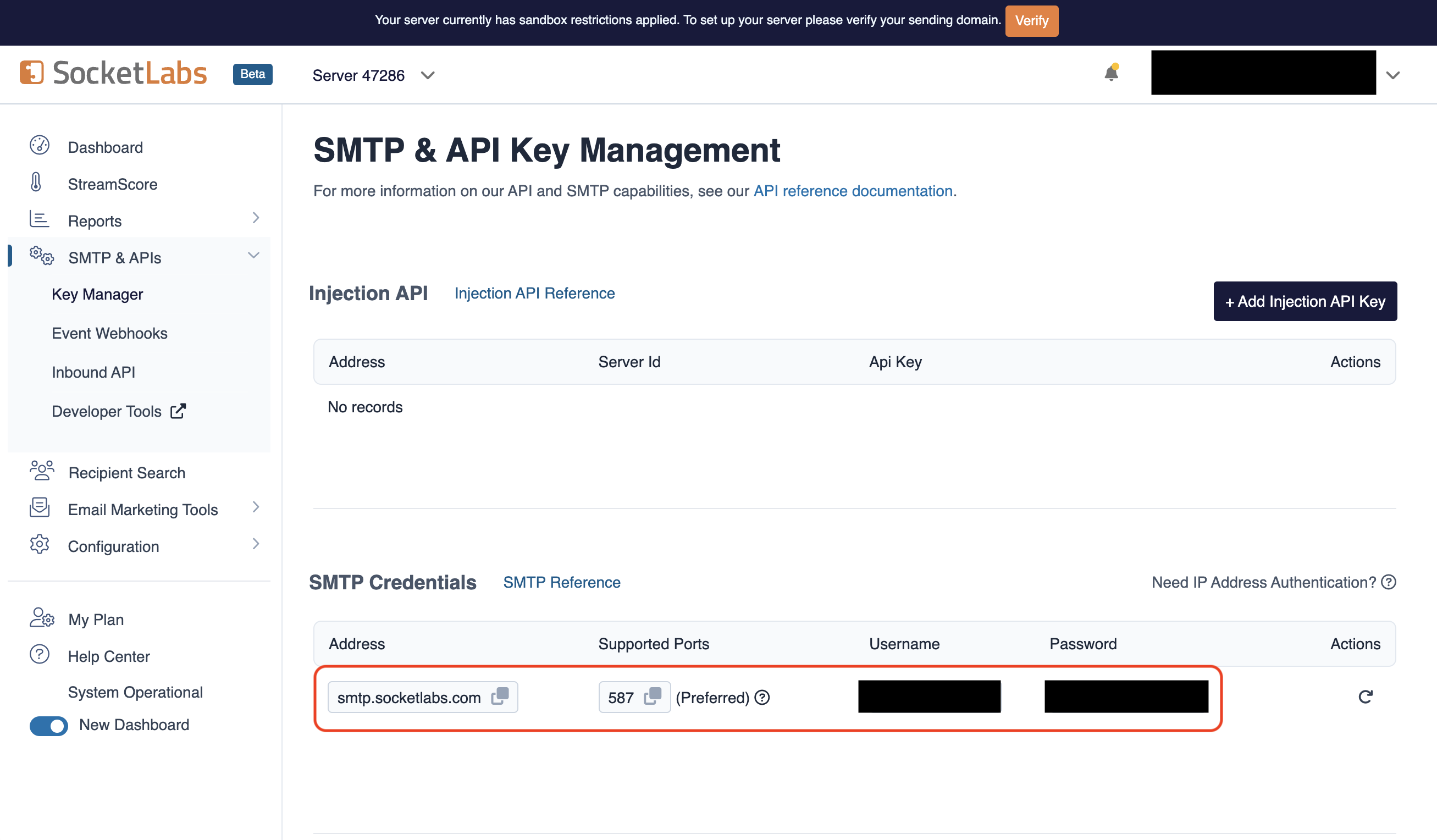
- With your SocketLabs SMTP credentials, you can now set up your SMTP environment variables:
The
SMTP_FROM_ADDRESS environment variable should be an email for an
authenticated domain under Configuration > Domain Management in SocketLabs.
For example, if you’re using SocketLabs in sandbox mode, then you may use an
email like team@sandbox.socketlabs.dev.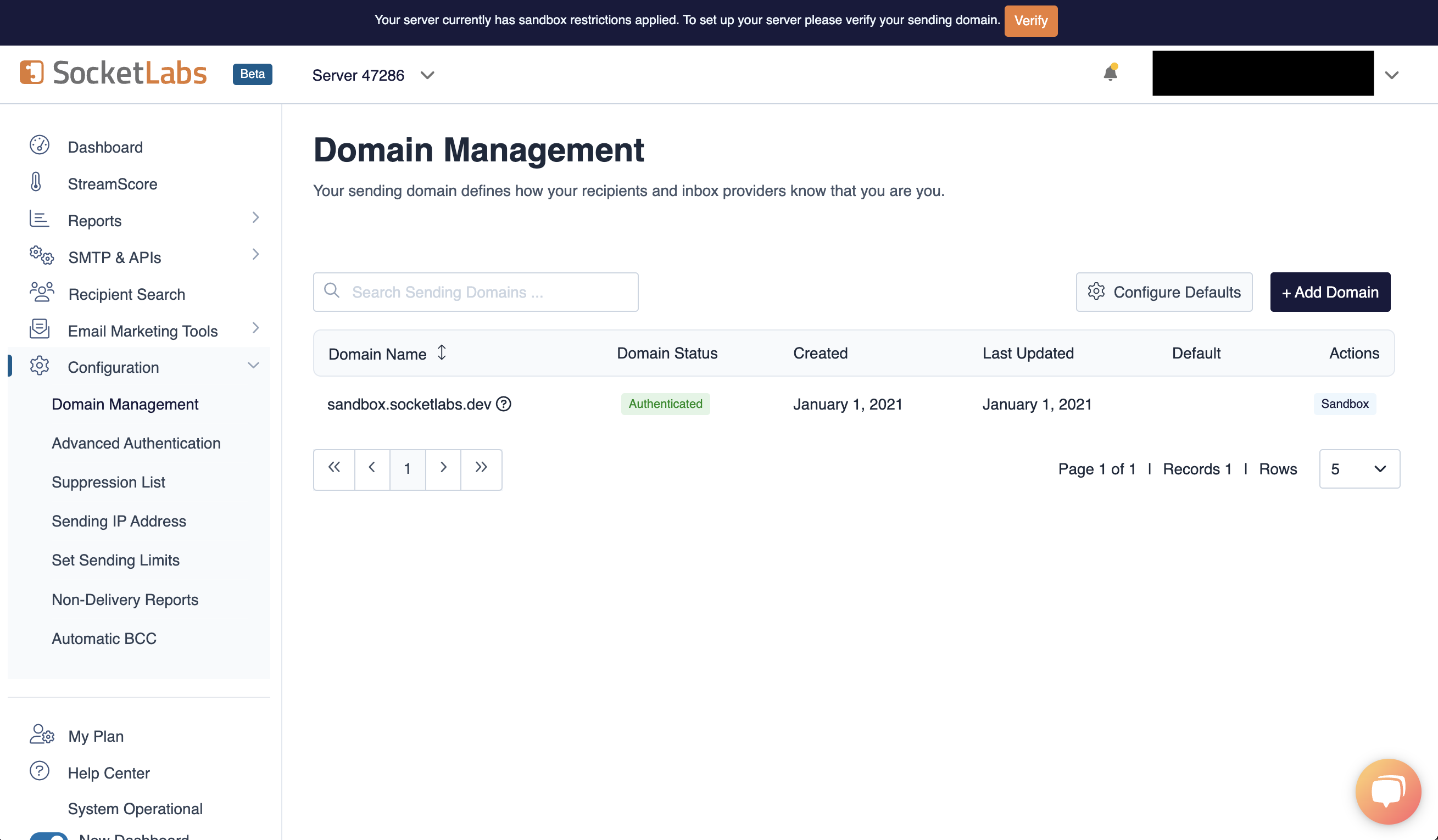
Remember that you will need to restart Infisical for this to work properly.
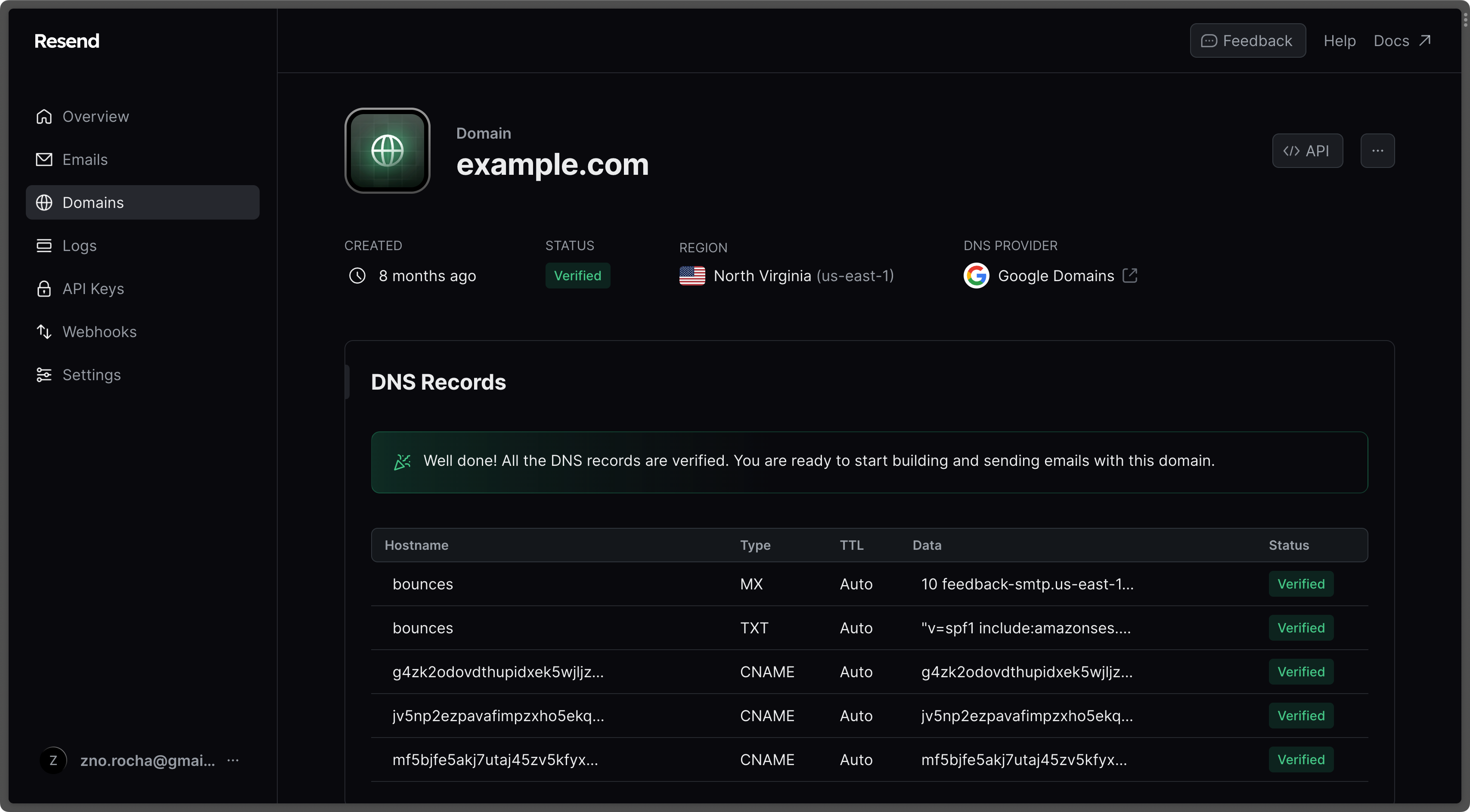
Resend
Resend
Gmail
Gmail
Create an account and enable “less secure app access” in Gmail Account Settings > Security. This will allow
applications like Infisical to authenticate with Gmail via your username and password. With your Gmail username and password, you can set your SMTP environment variables:
With your Gmail username and password, you can set your SMTP environment variables:
 With your Gmail username and password, you can set your SMTP environment variables:
With your Gmail username and password, you can set your SMTP environment variables:Office365
Office365
- Create an account and configure Office365 to send emails.
- With your login credentials, you can now set up your SMTP environment variables:
Zoho Mail
Zoho Mail
- Create an account and configure Zoho Mail to send emails.
- With your email credentials, you can now set up your SMTP environment variables:
You can use either your personal Zoho email address like
you@zohomail.com or
a domain-based email address like you@yourdomain.com. If using a
domain-based email address, then please make sure that you’ve configured and
verified it with Zoho Mail.Remember that you will need to restart Infisical for this to work properly.
SSO based login
By default, users can only login via email/password based login method. To login into Infisical with OAuth providers such as Google, configure the associated variables.Google
Follow detailed guide to configure Google SSO
OAuth2 client ID for Google login
OAuth2 client secret for Google login
Github
Github
Follow detailed guide to configure GitHub SSO
OAuth2 client ID for GitHub login
OAuth2 client secret for GitHub login
Gitlab
Gitlab
Follow detailed guide to configure GitLab SSO
OAuth2 client ID for GitLab login
OAuth2 client secret for GitLab login
URL of your self-hosted instance of GitLab where the OAuth application is registered
Okta SAML
Okta SAML
Requires enterprise license. Please contact team@infisical.com to get more information.
Azure SAML
Azure SAML
Requires enterprise license. Please contact team@infisical.com to get more information.
JumpCloud SAML
JumpCloud SAML
Requires enterprise license. Please contact team@infisical.com to get more information.
Configure SAML organization slug to automatically redirect all users of your Infisical instance to the identity provider.
Native secret integrations
To help you sync secrets from Infisical to services such as Github and Gitlab, Infisical provides native integrations out of the box.Heroku
Heroku
Vercel
Vercel
Netlify
Netlify
Github
Github
Bitbucket
Bitbucket
GCP Secrets Manager
GCP Secrets Manager
Azure
Azure