- Infisical (you can use Infisical Cloud or a self-hosted instance of Infisical) to store your secrets.
Project Setup
To begin, we need to set up a project in Infisical and add secrets to an environment in it.Create a project
- Create a new project in Infisical.
-
Add a secret to the development environment of this project so we can pull it back for local development. In the Secrets Overview page, press Explore Development and add a secret with the key
NEXT_PUBLIC_NAMEand valueYOUR_NAME. -
Add a secret to the production environment of this project so we can sync it to Vercel. Switch to the Production environment and add a secret with the key
NEXT_PUBLIC_NAMEand valueANOTHER_NAME.
Create a Next.js app
Initialize a new Node.js app. We can usecreate-next-app to initialize an app called infisical-nextjs.
- JavaScript
- TypeScript
pages/_app.js, lets add a console.log() to print out the environment variable in the browser console.
- JavaScript
- TypeScript
Infisical CLI for local development environment variables
We’ll now use the Infisical CLI to fetch secrets from Infisical into your Next.js app for local development.CLI Installation
Follow the instructions for your operating system to install the Infisical CLI.- MacOS
- Windows
- Alpine
- RedHat/CentOs/Amazon
- Debian/Ubuntu
- Arch Linux
Use brew package manager
Login
Authenticate the CLI with the Infisical platform using your email and password.Initialization
Run theinit command at the root of the Next.js app. This step connects your local project to the project on the Infisical platform and creates a infisical.json file containing a reference to that latter project.
Start the Next.js app with secrets injected as environment variables
dev; you can inject secrets from different
environments by modifying the env flag as per the CLI documentation.
At this stage, you know how to use the Infisical CLI to inject secrets into your Next.js app for local development.
Infisical-Vercel integration for production environment variables
We’ll now use the Infisical-Vercel integration send secrets from Infisical to Vercel as production environment variables.Infisical-Vercel integration
To begin we have to import the Next.js app into Vercel as a project. Follow these instructions to deploy the Next.js app to Vercel. Next, navigate to your project’s integrations tab in Infisical and press on the Vercel tile to grant Infisical access to your Vercel account.
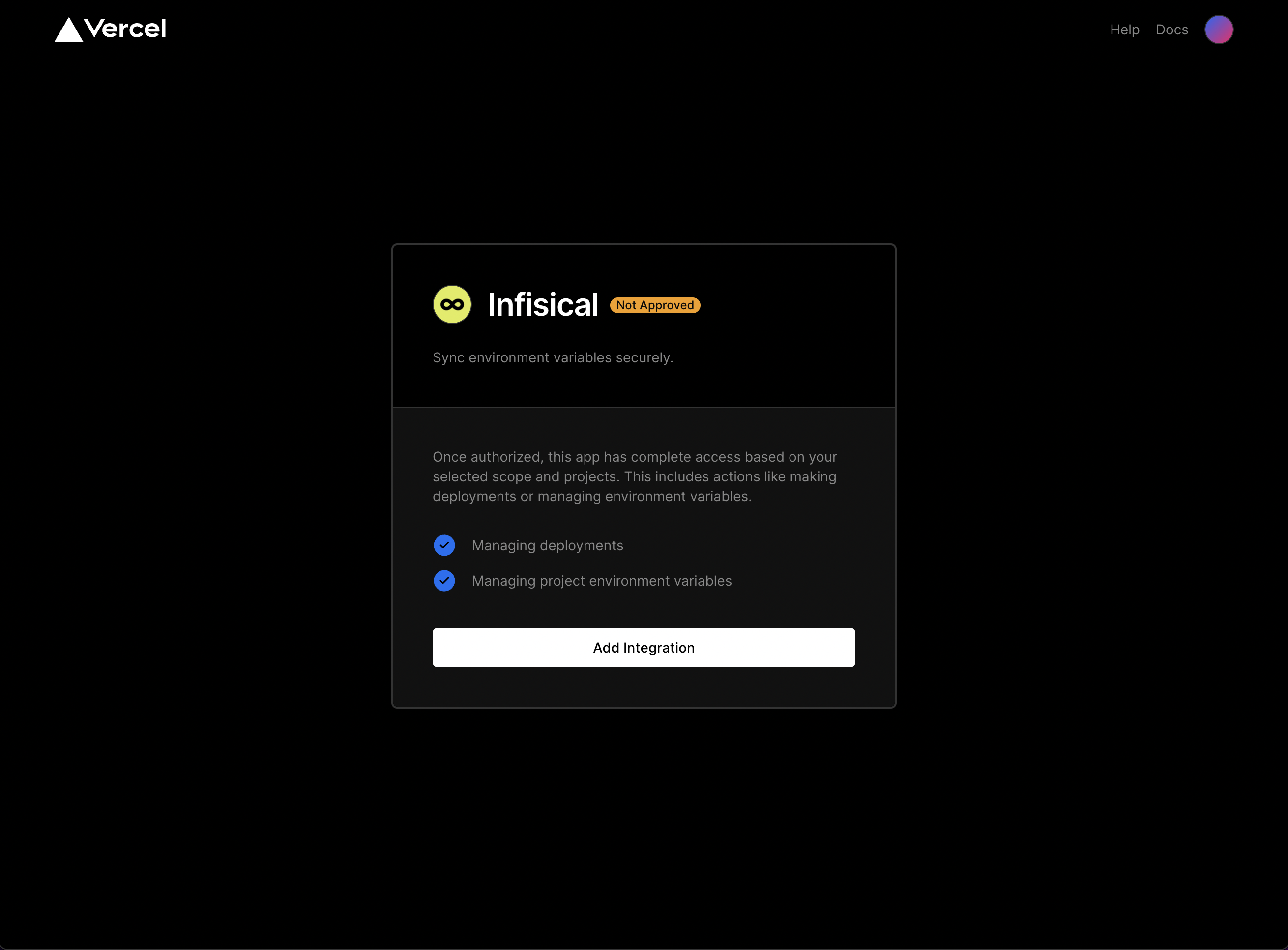
Opting in for the Infisical-Vercel integration will break end-to-end encryption since Infisical will be able to read
your secrets. This is, however, necessary for Infisical to sync the secrets to Vercel.Your secrets remain encrypted at rest following our security guide mechanics.
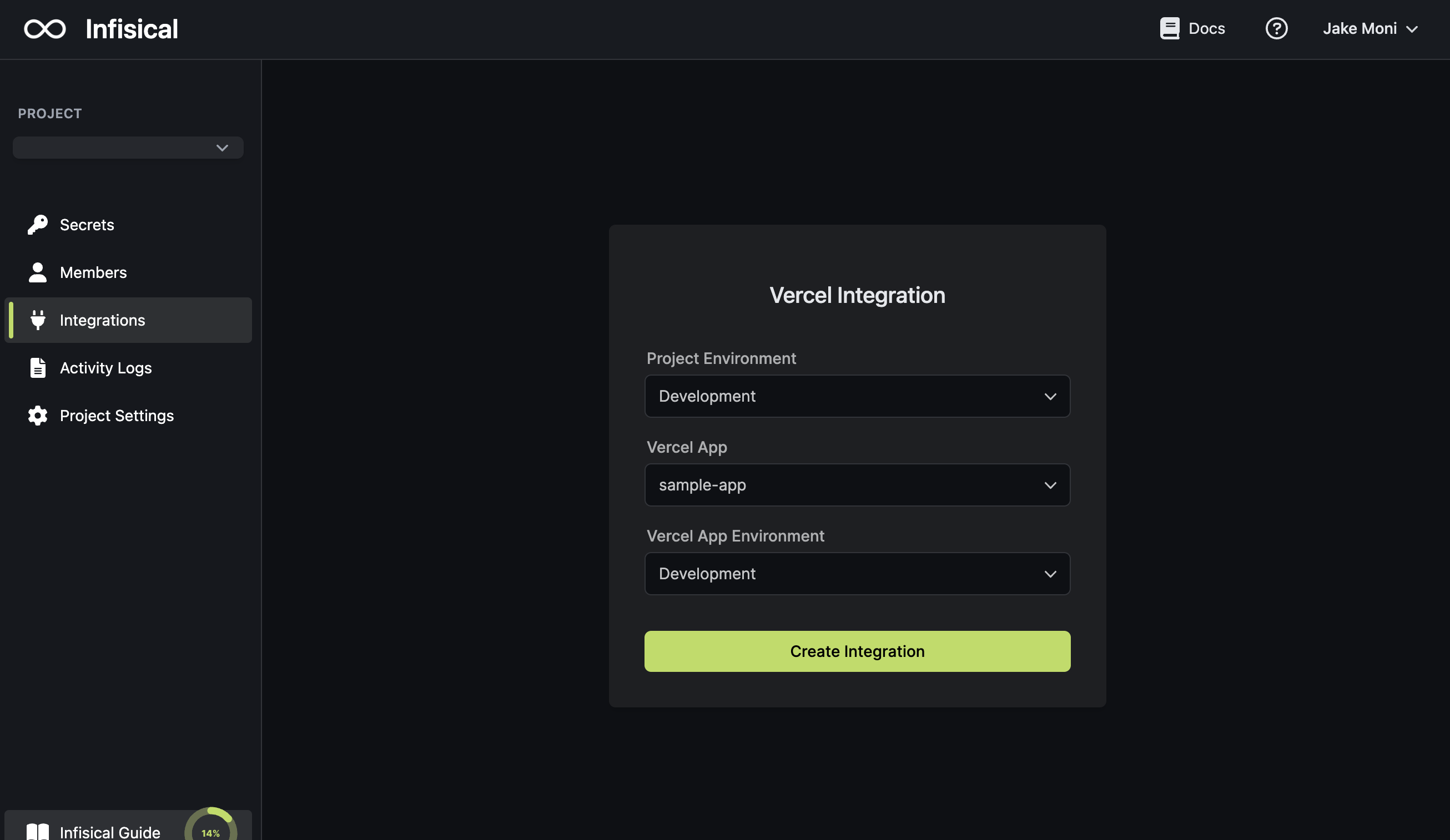
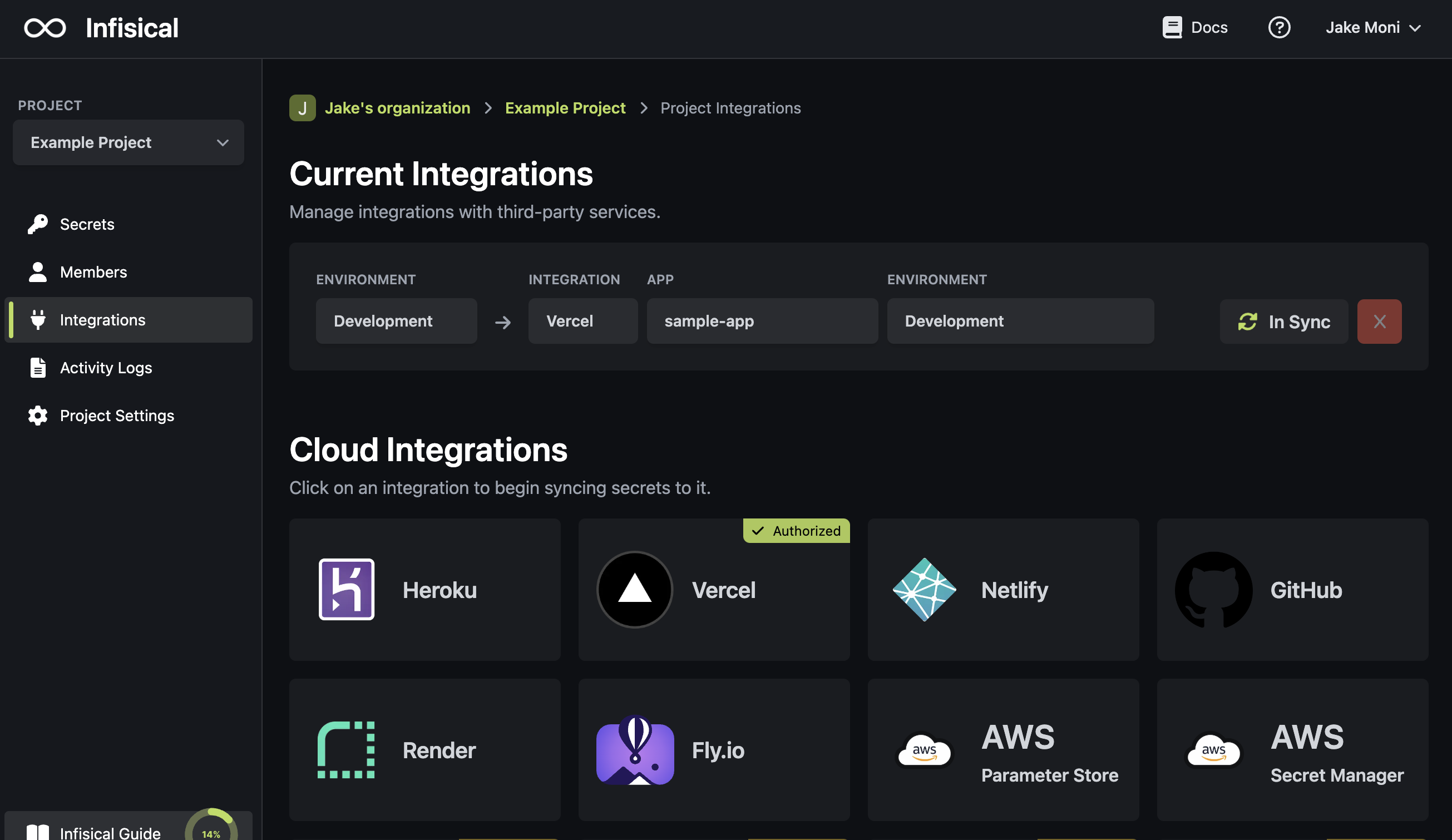 You should now see your secret from Infisical appear as production environment variables in your Vercel project.
At this stage, you know how to use the Infisical-Vercel integration to sync production secrets from Infisical to Vercel.
You should now see your secret from Infisical appear as production environment variables in your Vercel project.
At this stage, you know how to use the Infisical-Vercel integration to sync production secrets from Infisical to Vercel.
FAQ
Why should I use Infisical if I can centralize all my Next.js + Vercel environment variables across all environments directly in Vercel?
Why should I use Infisical if I can centralize all my Next.js + Vercel environment variables across all environments directly in Vercel?
Vercel does not specialize in secret management which means it lacks many useful features for effectively managing environment variables.
Here are some features that teams benefit from by using Infisical together with Vercel:
- Audit logs: See which team members are creating, reading, updating, and deleting environment variables across all environments.
- Versioning and point in time recovery: Rolling back secrets and an entire project state.
- Overriding secrets that should be unique amongst team members.
Is opting out of end-to-end encryption for the Infisical-Vercel integration safe?
Is opting out of end-to-end encryption for the Infisical-Vercel integration safe?
Yes. Your secrets are still encrypted at rest. To note, most secret managers actually don’t support end-to-end encryption.Check out the security guide.

