Infisical connects to Vault via the AppRole auth method.Currently, each Infisical project can only point and sync secrets to one Vault cluster / namespace
but with unlimited integrations to different paths within it.This tutorial makes use of Vault’s UI but, in principle, instructions can executed via
Vault CLI or API call.Lastly, you should note that we provide a simple use-case and, in practice, you should adapt and extend it to your own Vault use-case and follow best practices, for instance when defining fine-grained ACL policies.
- Set up and add envars to Infisical Cloud
- Have experience with HashiCorp Vault.
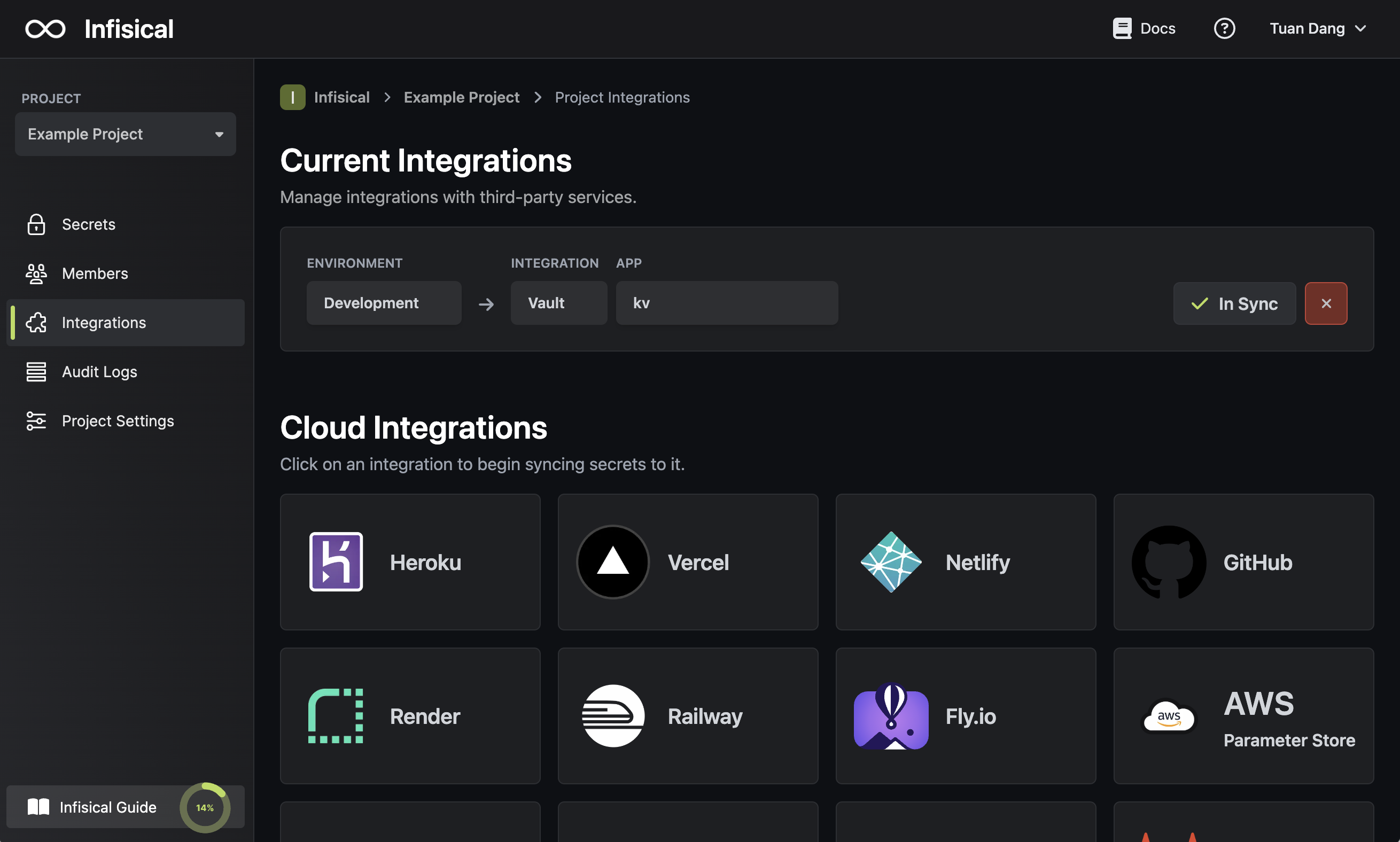
Navigate to your project’s integrations tab

Prepare Vault
This section mirrors the latter parts of the Vault quickstart provided by HashiCorp and uses sample names/values for demonstration. To begin, navigate to the cluster / namespace that you want to sync secrets to in Vault; we’ll use the defaultadmin namespace (in practice, we recommend creating a namespace and not using the default admin namespace).
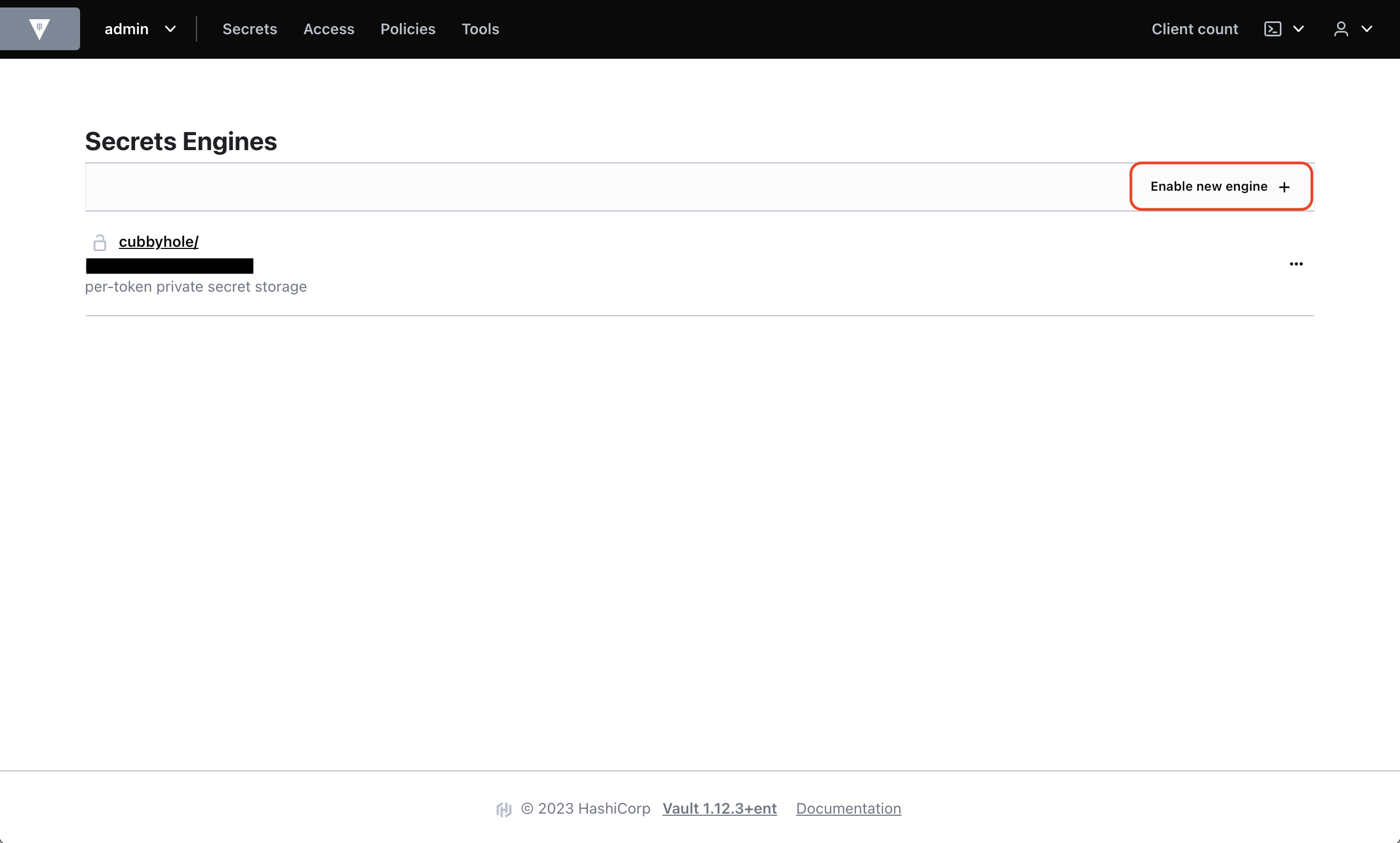
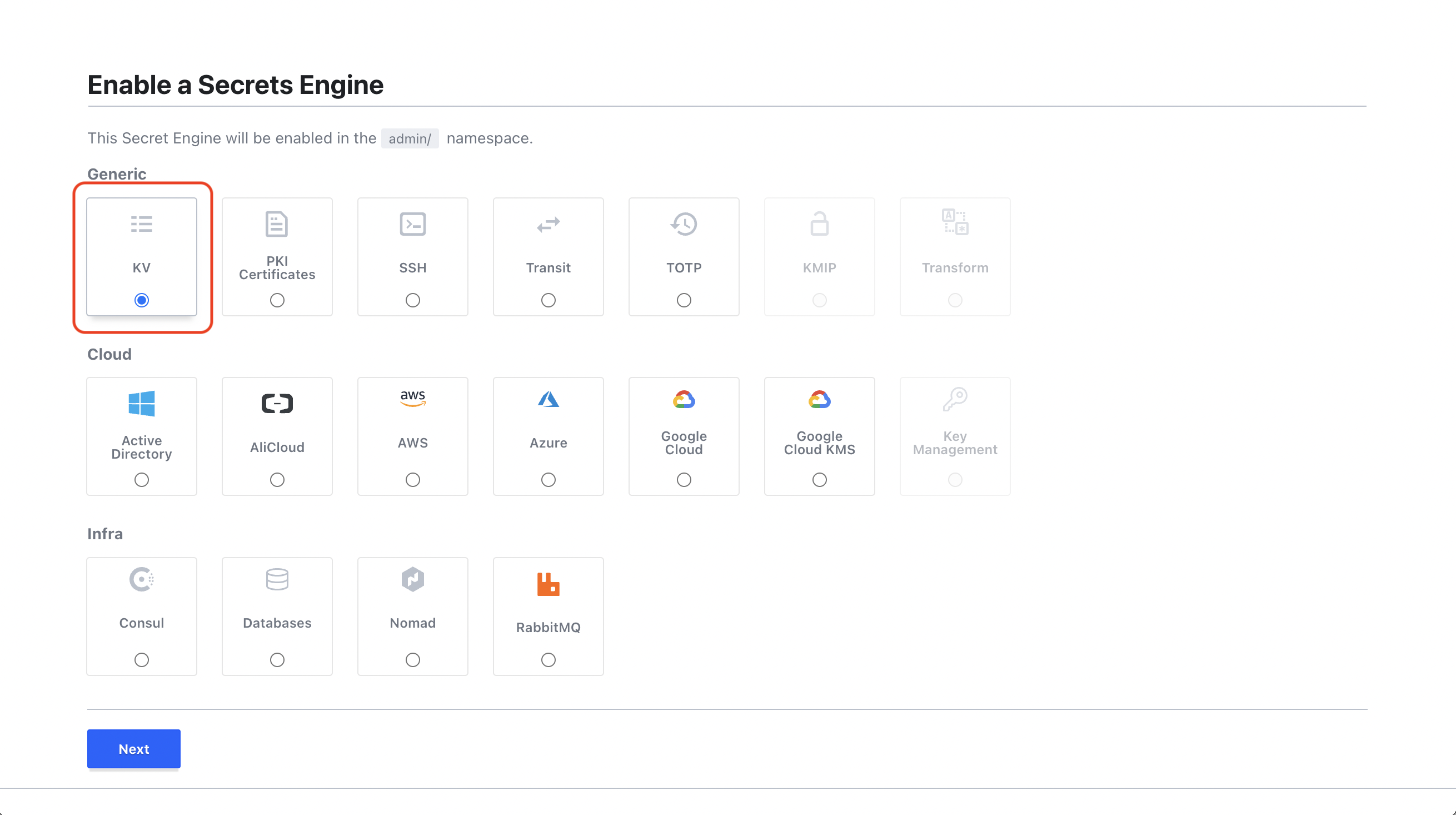
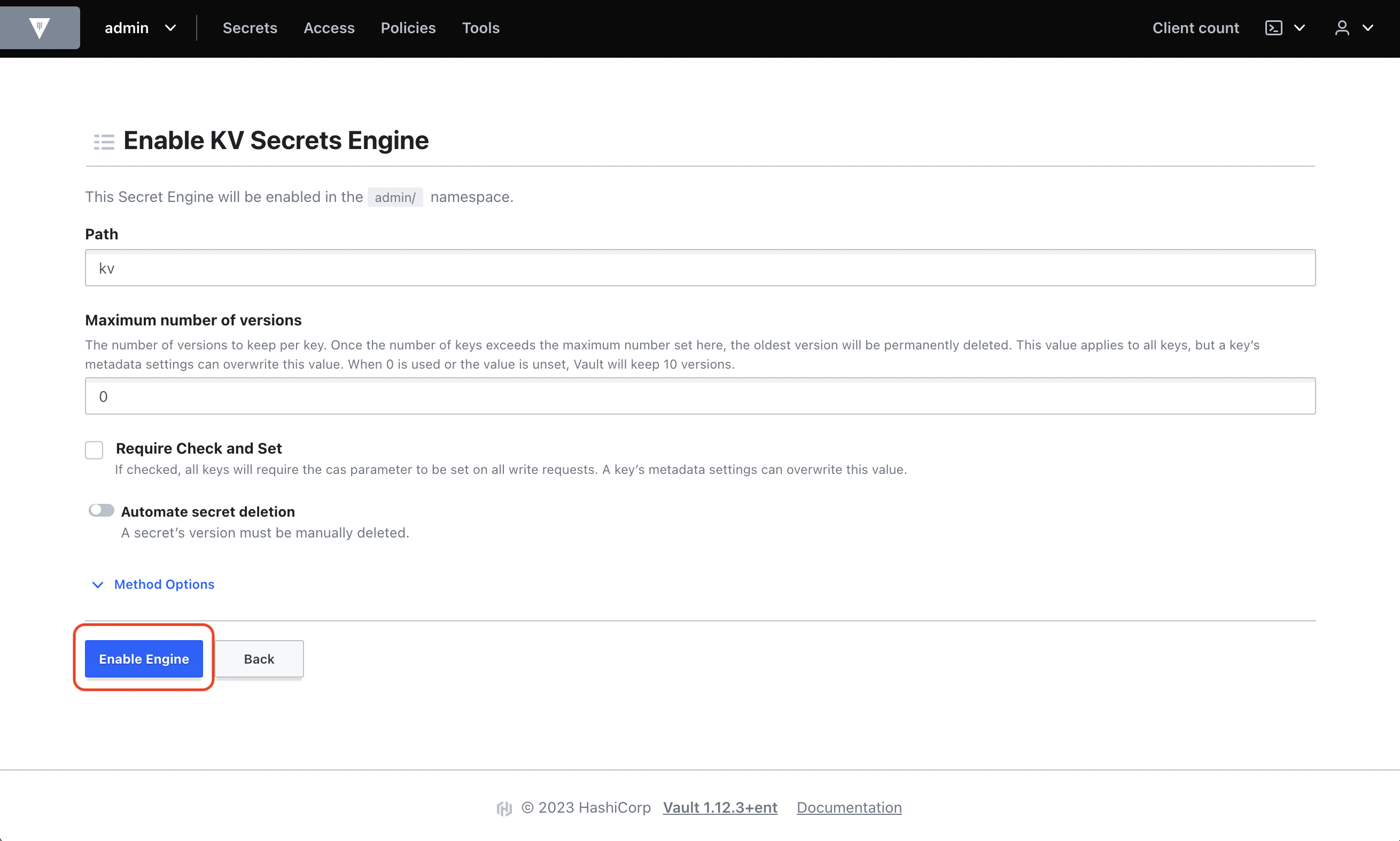
Enable KV Secrets Engine
In Secrets, enable a KV Secrets Engine at a path for Infisical to sync secrets to; we’ll use the pathkv.
Enable the AppRole auth method
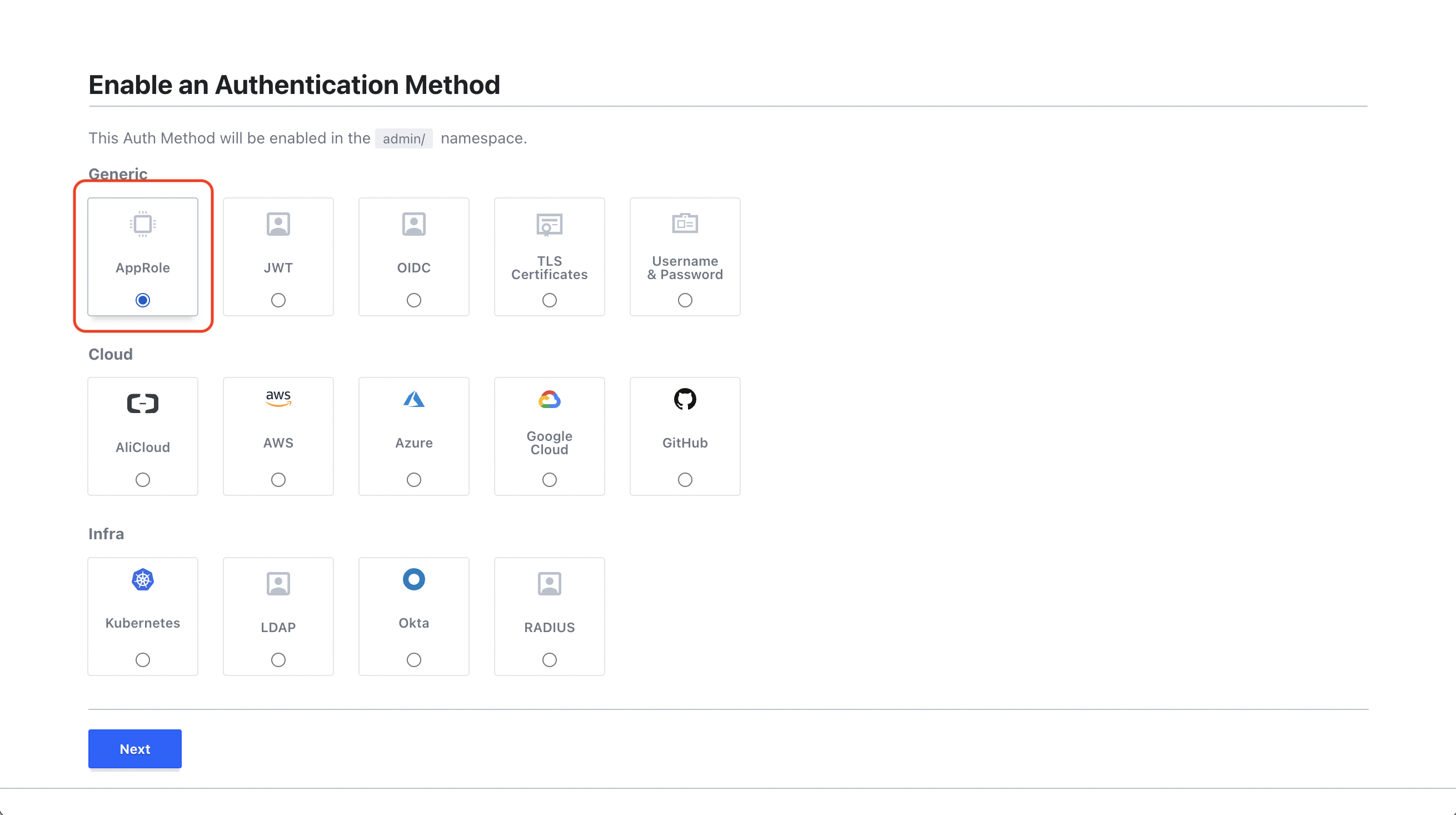
In Access > Auth Methods, enable the AppRole auth method.
Create an ACL Policy
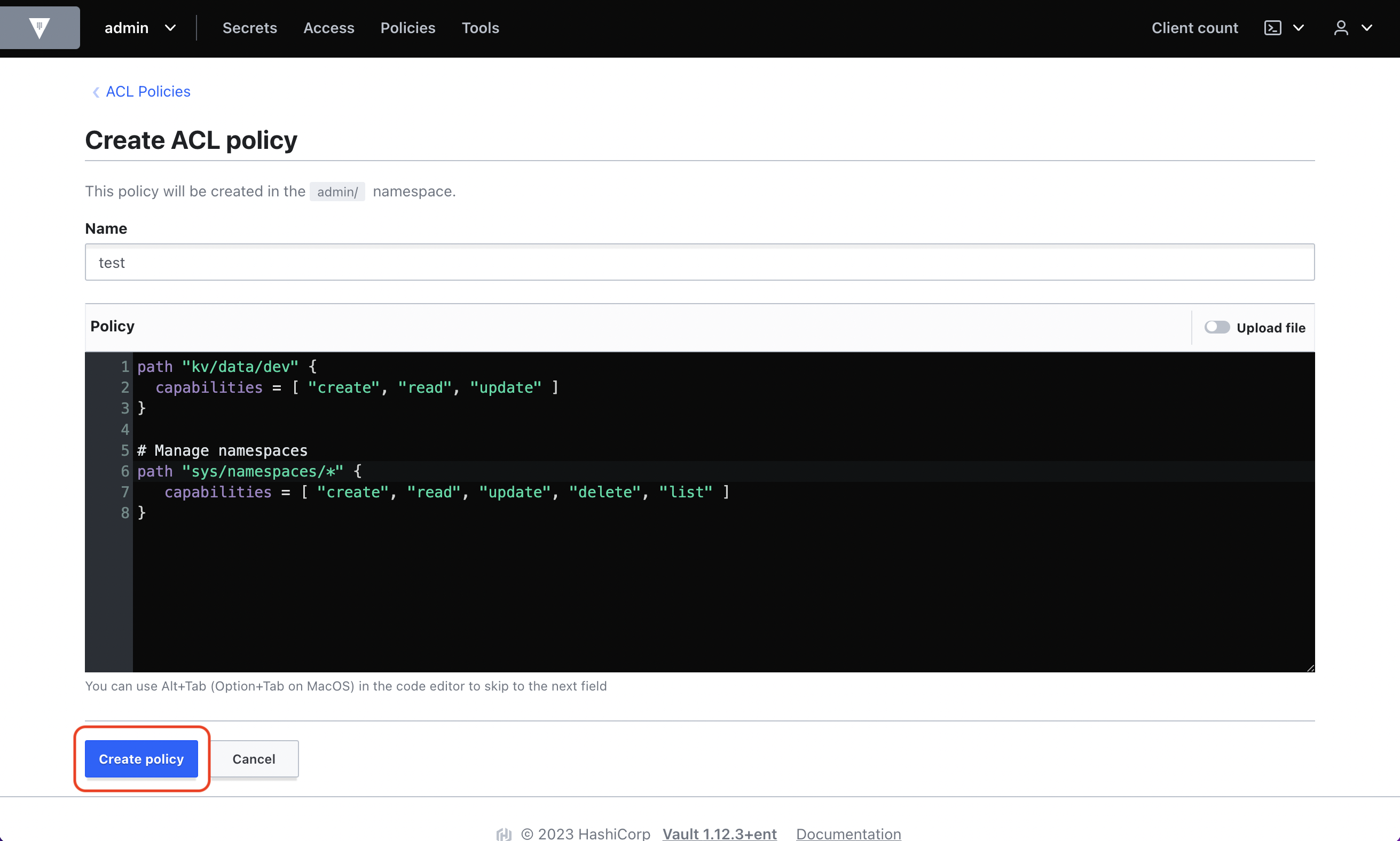
Now in Policies, create a new ACL policy scoped to the path(s) you wish Infisical to be able to sync secrets to. We’ll call the policytest and have it grant access to the dev path in the KV Secrets Engine where we will be syncing secrets to from Infisical.
kv comes from the path of the KV Secrets Engine that we enabled and dev is the chosen path within it
that we want to sync secrets to.
Create a role with the policy attached
We now create ainfisical role with the generated token’s time-to-live (TTL) set to 1 hour and can be renewed for up to 4 hours from the time of its creation.
- Click the Vault CLI shell icon (
>_) to open a command shell in the browser.
- Copy the command below.
- Paste the command into the command shell in the browser and press the enter button.
Generate a RoleID and SecretID
Finally, we need to generate a RoleID and SecretID (like a username and password) that Infisical can use to authenticate with Vault.- Click the Vault CLI shell icon (>_) again to open a command shell.
- Read the RoleID.
- Generate a new SecretID of the
infisicalrole.
Enter your Vault instance and authentication details
Back in Infisical, press on the HashiCorp Vault tile and input your Vault instance andinfisical role RoleID and SecretID.
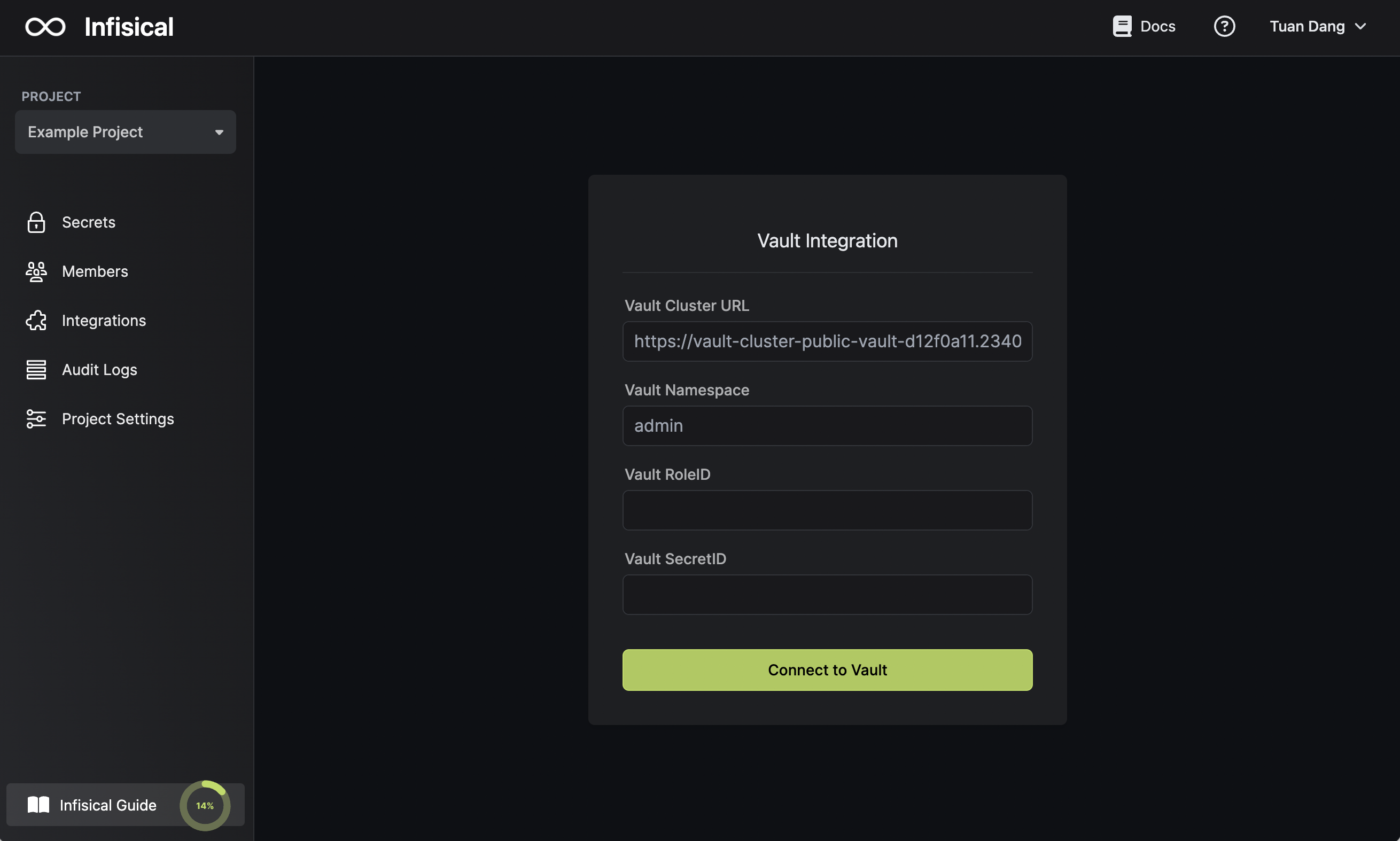 For additional details on each field:
For additional details on each field:
- Vault Cluster URL: The address of your cluster, either HCP or self-hosted.
- Vault Namespace: The Vault namespace you wish to connect to.
- Vault RoleID: The RoleID previously created for the
infisicalrole. - Vault SecretID: The SecretID previously created for the
infisicalrole.
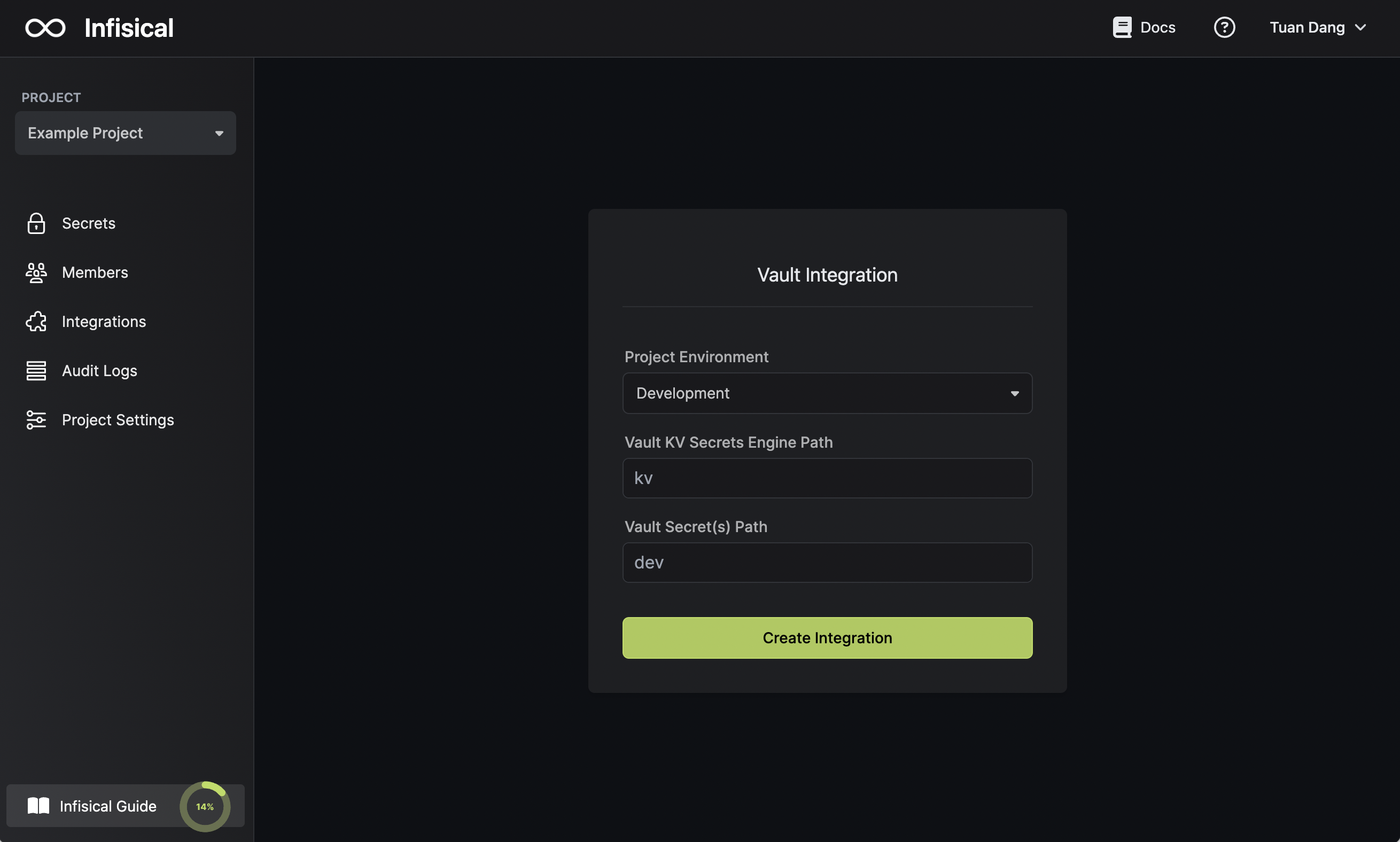
Start integration
Select which Infisical environment secrets you want to sync to Vault. For additional details on each field:- Vault KV Secrets Engine Path: the path at which you enabled the intended KV Secrets Engine; in this demonstration, we used
kv. - Vault Secret(s) Path: the path in the KV Secrets Engine that you wish to sync secrets to.